Almost half of the Internet users across the globe use ADSL routers/modems to connect to the Internet however, most of them are unaware of the fact that it has a serious vulnerability which can easily be exploited even by a noob hacker just like you. In this post I will show you how to exploit a common vulnerability that lies in most ADSL routers so as to gain complete access to the router settings and ISP login details.
Almost half of the Internet users across the globe use ADSL routers/modems to connect to the Internet however, most of them are unaware of the fact that it has a serious vulnerability which can easily be exploited even by a noob hacker just like you. In this post I will show you how to exploit a common vulnerability that lies in most ADSL routers so as to gain complete access to the router settings and ISP login details.
Every router comes with a username and password using which it is possible to gain access to the router settings and configure the device. The vulnerability actually lies in theDefault username and password that comes with the factory settings. Usually the routers come preconfigured from the Internet Service provider and hence the users do not bother to change the password later. This makes it possible for the attackers to gain unauthorized access and modify the router settings using a common set of default usernames and passwords. Here is how you can do it.
Before you proceed, you need the following tool in the process
Here is a detailed information on how to exploit the vulnerability of an ADSL router.
Step-1: Go to www.whatismyipaddress.com. Once the page is loaded you will find your IP address. Note it down.
Step-2: Open Angry IP Scanner, here you will see an option called IP Range: where you need to enter the range of IP address to scan for.
Step-3: Go to Tools->Preferences and select the Ports tab. Under Port selectionenter 80 (we need to scan for port 80). Now switch to the Display tab, select the option “Hosts with open ports only” and click on OK.

Step-4: Now click on Start. After a few minutes, the IP scanner will show a list of IPs with Port 80 open as shown in the below image.
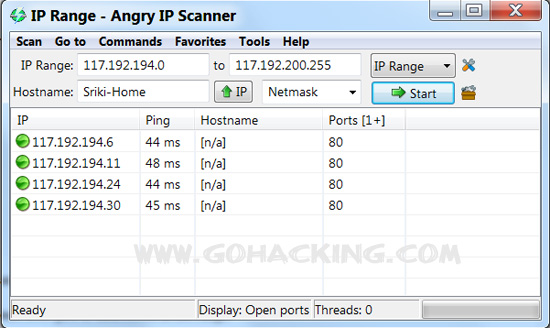 Step-5: Now copy any of the IP from the list, paste it in your browser’s address bar and hit enter. A window will popup asking for username and password. Since most users do not change the passwords, it should most likely work with the default username and password. For most routers the default username-password pair will be admin-admin or admin-password.
Step-5: Now copy any of the IP from the list, paste it in your browser’s address bar and hit enter. A window will popup asking for username and password. Since most users do not change the passwords, it should most likely work with the default username and password. For most routers the default username-password pair will be admin-admin or admin-password.
Just enter the username-password as specified above and hit enter. If you are lucky you should gain access to the router settings page where you can modify any of the router settings. The settings page can vary from router to router. A sample router settings page is shown below.
If you do not succeed to gain access, select another IP from the list and repeat the step-5. Atleast 1 out of 5 IPs will have a default password and hence you will surely be able to gain access.
What can an Attacker do by Gaining Access to the Router Settings?
By gaining access to the router settings, it is possible for an attacker to modify any of the router settings which results in the malfunction of the router. As a result the target user’s computer will be disconnected from the Internet. In the worst case the attacker can copy the ISP login details from the router to steal the Internet connection or play any kind of prank with the router settings. So the victim has to reconfigure the router in order to bring it back to action.
The Verdict:
If you are using an ADSL router to connect to the Internet, it is highly recommended that you immediately change your password to prevent any such attacks in the future. Who knows, you may be the next victim of such an attack.
Since the configuration varies from router to router, you need to contact your ISP for details on how to change the password for your model.
All the information provided in this post are for educational purposes only. Please do not use this information for illegal purposes.